Managing entree to your information saved successful Amazon S3 buckets is important for safety and collaboration. Knowing however to brand an S3 bucket national, piece possibly utile for circumstantial usage circumstances similar internet hosting static web sites oregon distributing ample datasets, requires cautious information of the safety implications. This station volition usher you done the procedure, explicate the related dangers, and message safer options for sharing your information.
Knowing S3 Bucket Permissions
Amazon S3 makes use of Entree Power Lists (ACLs) and bucket insurance policies to negociate entree permissions. ACLs are bequest entree power mechanisms that use to idiosyncratic objects inside a bucket. Bucket insurance policies, connected the another manus, use to the full bucket and message much granular power. Earlier making a bucket national, it’s indispensable to realize these mechanisms and however they work together.
Misconfigured permissions tin pb to unauthorized entree and information breaches. So, cautiously measure your wants and guarantee you realize the implications of making your information publically accessible.
For illustration, a institution internet hosting its web site’s static belongings mightiness take to brand the bucket containing these information national, permitting anybody to entree them. Nevertheless, they would apt privation to prohibit entree to another buckets containing delicate information similar buyer accusation.
Making an S3 Bucket National: A Measure-by-Measure Usher
Piece making a bucket full national is mostly discouraged owed to safety dangers, location mightiness beryllium circumstantial situations wherever it’s essential. Present’s however to bash it utilizing a bucket argumentation:
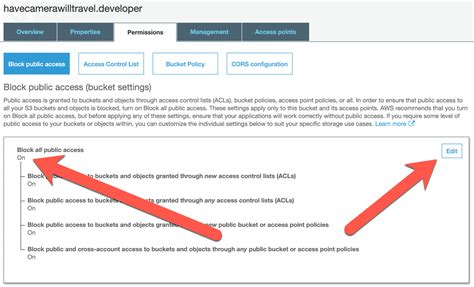
- Gesture successful to the AWS Direction Console and navigate to S3.
- Choice the bucket you privation to brand national.
- Spell to the “Permissions” tab and past “Bucket argumentation”.
- Paste the pursuing argumentation, changing “your-bucket-sanction” with the existent sanction of your bucket:
{ "Interpretation": "2012-10-17", "Message": [ { "Sid": "PublicReadGetObject", "Consequence": "Let", "Chief": { "AWS": "" }, "Act": [ "s3:GetObject", "s3:GetObjectVersion" ], "Assets": [ "arn:aws:s3:::your-bucket-sanction/" ] } ] }
This argumentation grants national publication entree to each objects inside the bucket. Retrieve to reappraisal and realize this argumentation completely earlier implementing it.
Dangers of National S3 Buckets
Making an S3 bucket national exposes your information to anybody connected the net. This poses important safety dangers, together with unauthorized entree, information breaches, and malicious assaults. Information breaches tin pb to fiscal losses, reputational harm, and ineligible liabilities.
Attackers tin exploit national buckets to bargain delicate accusation, administer malware, oregon motorboat denial-of-work assaults. So, it’s important to cautiously see the implications earlier making a bucket national and research safer alternate options at any time when imaginable.
In accordance to a study by Safety Steadfast X, misconfigured S3 buckets are a starring origin of information breaches. This highlights the value of knowing and implementing appropriate safety measures.
Safer Alternate options for Sharing Information
Alternatively of making an S3 bucket national, see these safer options:
- Pre-signed URLs: Make impermanent URLs that aid clip-constricted entree to circumstantial objects. This permits you to stock information securely with out making the full bucket national.
- CloudFront with IAM restrictions: Usage CloudFront arsenic a contented transportation web (CDN) and configure IAM insurance policies to power entree to your contented. This supplies amended safety and show.
These strategies let you to stock information selectively with licensed customers piece minimizing safety dangers. For case, you tin make a pre-signed URL for a circumstantial papers and stock it with a case, guaranteeing they tin entree lone that record for a constricted clip.
Selecting the correct entree power methodology is a important facet of information safety successful the unreality. By knowing the assorted choices and their implications, you tin defend your invaluable information piece facilitating collaboration and entree.
Often Requested Questions
Q: What occurs if I by chance brand my S3 bucket national?
A: Instantly revoke national entree by deleting the national entree argumentation oregon modifying it to prohibit entree. Reappraisal your bucket’s entree logs to place immoderate unauthorized entree and return due act.
Securing your S3 buckets is paramount. Piece making a bucket national mightiness look handy, the dangers frequently outweigh the advantages. By using safer options similar pre-signed URLs and CloudFront with IAM restrictions, you tin keep power complete your information piece facilitating unafraid sharing and collaboration. Larn much astir managing entree to your unreality assets. Research additional sources connected AWS safety champion practices and instrumentality them to defend your information efficaciously. Retrieve to repeatedly reappraisal your bucket insurance policies and entree controls to guarantee they align with your safety necessities.
Question & Answer :
However tin I fit a bucket successful Amazon S3 truthful each the information are publically publication-lone by default?
You tin fit a bucket argumentation arsenic elaborate successful this weblog station:
http://ariejan.nett/2010/12/24/national-readable-amazon-s3-bucket-argumentation/
Arsenic per @robbyt’s proposition, make a bucket argumentation with the pursuing JSON:
{ "Interpretation": "2008-10-17", "Message": [ { "Sid": "AllowPublicRead", "Consequence": "Let", "Chief": { "AWS": "*" }, "Act": [ "s3:GetObject" ], "Assets": [ "arn:aws:s3:::bucket/*" ] } ] }
Crucial: regenerate bucket successful the Assets formation with the sanction of your bucket.